Improving instance security using two-factor authentication with Duo (2FA)
In addition to protecting your Triton cloud account in the portal with two-factor authentication, you can also protect your instances with two-factor authentication when connecting to your instance through SSH. Using Duo, verification will be sent to your mobile device. This document describes how to add 2nd factor authentication to SmartOS using the Duo PAM module.
What is two-factor authentication for SSH and how does it work on SmartOS?
SmartOS libpam allows adding additional methods of verification when connecting using SSH. The default method of verifying identity for SSH is using a public and private key pair. This allows for passwordless authentication as SSH keys are much harder to guess than passwords and are less susceptible to brute force attacks. Private keys can be further protected with a passphrase so that if your private key is compromised or stolen, it cannot be used without knowing the passphrase. Two-factor authentication does not require the use of keys, you can use a normal password in addition to a one-time-password, however as stated earlier passwords are not as secure as using keys.
Duo PAM Library for two-factor authentication
Using the Duo PAM library can add another layer of security to your instance. The following setup method will use the default key verification method as well as adding another factor using one-time-passwords (OTP) or push notifications generated through the Duo application. When using Duo for two-factor authentication, a Duo account is required and the instance must be able to contact the Duo servers.
Installing Duo on SmartOS using pkgsrc and configuration for SSH/PAM (root user)
The Duo library is available in pkgsrc on SmartOS. The command pkgin install duo-unix-compat32-1.0 will install the Duo library. After installation via pkgsrc the following steps need to be taken to configure SSH to use Duo authentication:
-
Ensure you have created an account on Duo's website. If you have already created an account sign in to your Duo Account.
-
On your Duo dashboard find the Add New button and in the dropdown select Application
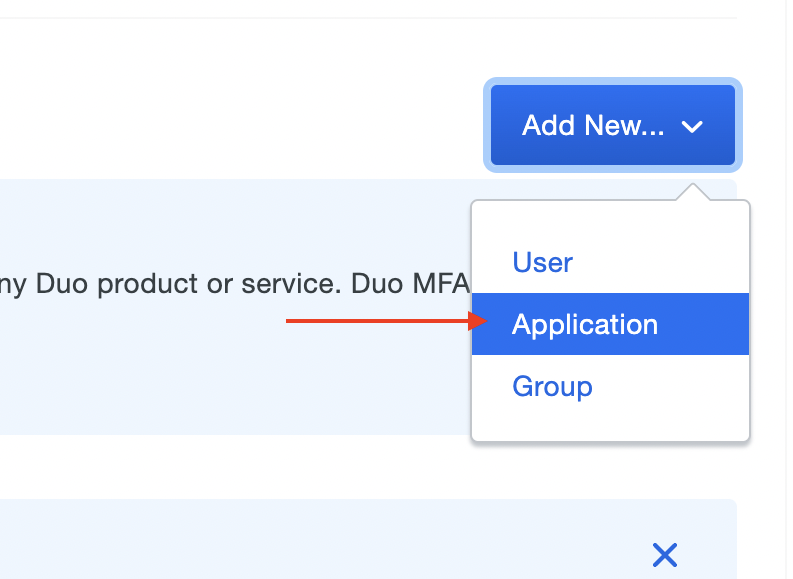
-
In Protect an Application use the search bar to search for UNIX Application, and then click on the protect button.
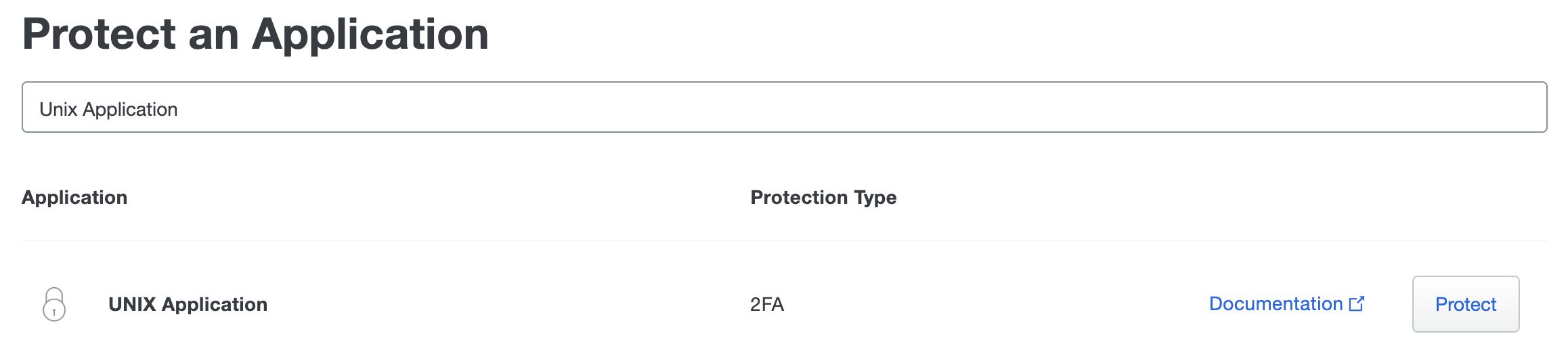
-
In the Unix Application screen, you will be presented with three items: Integration Key, Secret Key, and API Hostname. These items will need to be placed in the
/opt/local/etc/pam_duo.conffile in their designated lines, and uncomment the pushinfo = yes line.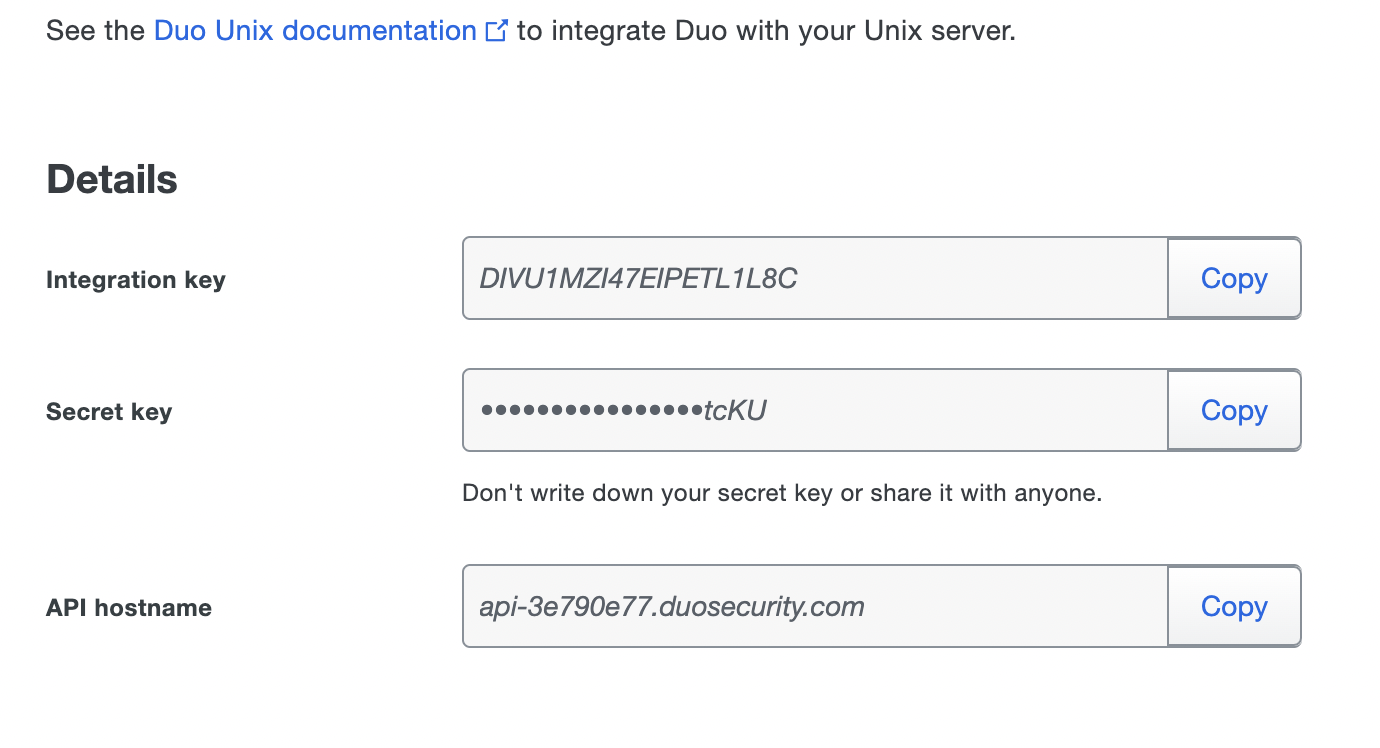
[duo] ; Duo integration key ikey = INTEGRATIONKEYGOESHERE ; Duo Secret key skey = SECRETKEYGOESHERE ; Duo API host host = APIHOSTGOESHERE ; `failmode = safe` In the event of errors with this configuration file or connection to the duo service ; this mode will allow login without 2FA. ; `failmode = secure` This mode will deny access in the above cases. Misconfigurations with this setting ; enabled may result in you being locked out of your system. failmode = safe ; Send command for Duo Push authentication ; For push notifications uncomment line below pushinfo = yes -
After adding the appropriate keys, the next step is to add the following lines to
/etc/pam.conf:sshd-kbdint auth required /opt/local/lib/security/i386/pam_duo.so sshd-kbdint auth required pam_allow.so.1 -
Next, configure
sshdto require key authentication plus Duo. In your/etc/ssh/sshd_configfile change the optionPermitRootLogin without-passwordtoPermitRootLogin yes. At the end of your/etc/ssh/sshd_configadd the following lines:ChallengeResponseAuthentication yes AuthenticationMethods publickey,keyboard-interactive -
After completing the above steps, restart the ssh service by using the
svcadm restart sshcommand. To ensure that the ssh service restarted correctly use the commandsvcs -xv, this will show if the ssh service is in maintenance. If the ssh service is in maintenance, double check the/etc/ssh/sshd_configto ensure there are no syntax errors, and then usesvcadm clear sshand thensvcadm restart ssh. -
To ensure you are not locked out of your instance, in a separate terminal window ssh into your instance and if configured correctly you will be presented with a Duo prompt.
Enter a passcode or select one of the following options: 1. Duo Push to 555-555-1234 2. SMS Passcodes to 555-555-1234 Passocde or opiton (1-2):At the Duo Prompt select your option of push or SMS message. You should now be at a prompt and you have successfully configured two-factor authentication for the root user using Duo.
